Simplifying access management with RFID authentication | USA
Is your work site vulnerable to security breaches?
Traceability
Need to prevent unauthorized access to secure areas
Anti-tampering
Protect devices and equipment from unapproved changes
Accurate records
Log and monitor user activity with timestamps
RFID authentication keeps areas and equipment secure
KW2D RFID reader
The KW2D RFID reader can be mounted directly on machinery or other equipment. Users must present a card or keyfob with an embedded RFID tag for the reader to identify and authenticate.
Register up to 500 RFID tags
Up to 255 authorization levels
IDEC tag recognition for added security
Dedicated software for configuration
View data logs on a compatible display

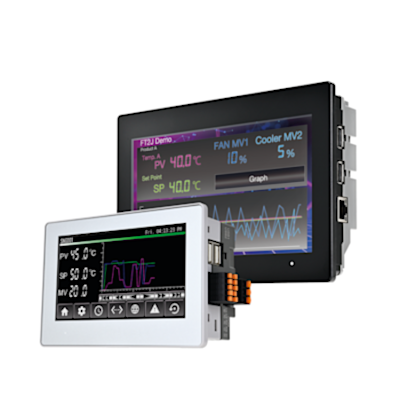
FT2J controller with operator interface
Data logs from an RFID system can be sent to a HMI, drastically reducing paperwork. Individual tag verifications are also communicated to that host device as data.
7-inch display, PCAP touch panel
Slim bezel design for maximum screen area
Dual CPUs for high-speed processing
Data sharing via Ethernet (network protocols)
IoT functionality: remote monitoring and notifications
In manufacturing, logistics, and other industries where security is paramount, industrial RFID systems efficiently manage and record:
Entry and exits (door access control systems)
Access to specific areas and equipment
User authority levels
Use of tools and controls (equipment tracking)
Changes to equipment settings
Inspection history
We provide a wide range of help and resources:
If you have questions or suggestions, we're here to listen.
Our sales and support teams are on hand to help.
All the technical documentation you need.